 Finance teams are finally embracing digital, but they must not be complacent about the risks associated with transformation. According to PWC, 53% of chief finance executives are looking to accelerate digital transformation in the next 12 months using data analytics, AI, automation, and cloud solutions to help drive standardization and intelligently automate as many manual processes as possible.1
Finance teams are finally embracing digital, but they must not be complacent about the risks associated with transformation. According to PWC, 53% of chief finance executives are looking to accelerate digital transformation in the next 12 months using data analytics, AI, automation, and cloud solutions to help drive standardization and intelligently automate as many manual processes as possible.1
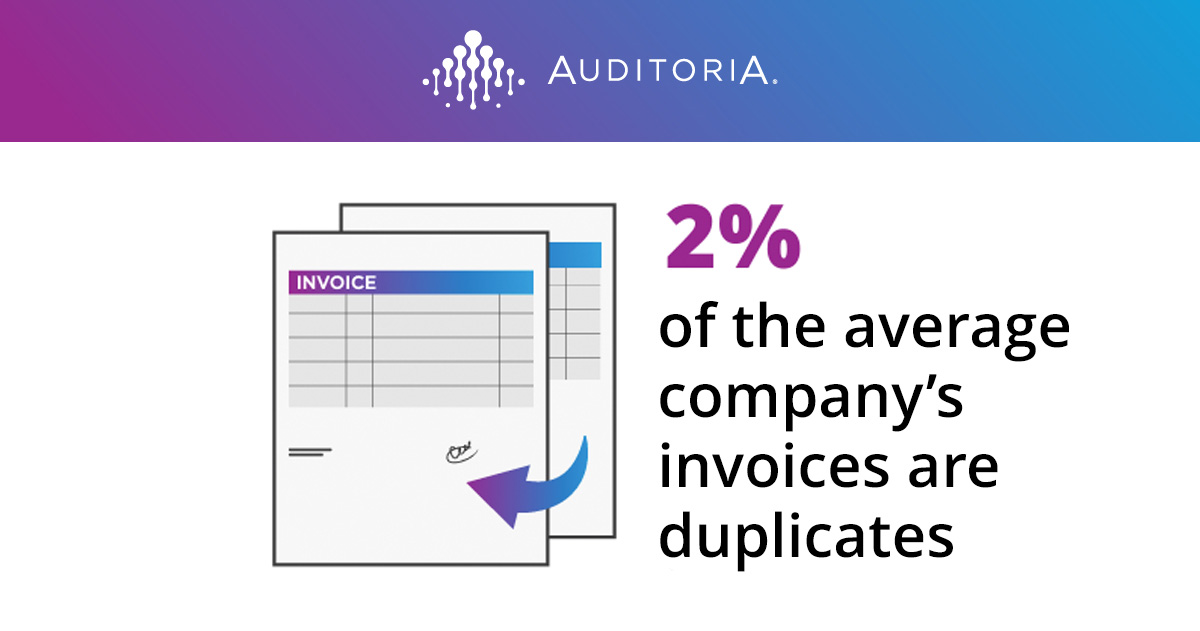
Clearly, it is vital that finance teams are trained to detect and avoid these scams. But the reality is human-error will likely always be a factor. Analysts estimate 12.5% of invoices that are processed manually end up being reworked,10 and 2% of the average company’s invoices are duplicates.11
The reality is human-error will likely always be a factor in exploitation by phishing and scammers.
Modern cyberattacks are generally automated, and adapt quickly to exploit new vulnerabilities, often playing on the emotions and sensitivities of humans. That is why implementing automation is a surprisingly effective bulwark against cyber attacks.
Not only does it reduce human-error, it removes the possibility of social engineering, as machines are simply not susceptible to emotional or psychological manipulation. This is not merely theoretical.
AI Adopters recognize how AI-driven insights and
AI-powered automation complement the expert level identification and response capabilities of their security subject matter experts.
- IBM Institute for Business Value13
IBM’s poll of leaders found that AI is helping them detect threats 30% faster. They are also significantly improving response times to incidents and the time to investigate.12
10 https://www.gocomet.com/blog/freight-invoice-errors-hidden-costs-affecting-your-bottom-line/
11 https://www.globaltrademag.com/8-ways-your-ap-process-leaks-spend-and-how-ai-can-prevent-it/
12 https://www.ibm.com/thought-leadership/institute-business-value/report/ai-cybersecurity
13 https://www.ibm.com/downloads/cas/9NGZA7GK